🧠 TL;DR
Sometimes weak passwords sneak through — yes, even for Domain Admins. This walkthrough shows you how to pull and crack NTDS.dit safely using Kali, hashcat, and a few trusty wordlists. Just tidy up when you’re done.
Overview
Let’s be honest — weak passwords pop up all the time. Maybe it’s a service account someone forgot about. Maybe it’s a Domain Admin who thinks “H@ckerM4n!” is clever. Either way, you don’t want to find out the hard way. Running internal password audits now and then helps spot these gaps before someone else does.
And yeah, you’ve probably got password policies, rotation schedules, and complexity rules. But as we all know, that doesn’t mean the passwords are actually any good.
Quick heads-up: most antivirus tools will complain about this process. Either disable it temporarily or give your security team a heads-up so they don’t freak out.
Prerequisites
Make sure you have a Kali Linux VM set up. It’s a solid choice for security auditing and has the tools we need pre-installed (or easy to install).
Tools Needed: Ensure impacket and hashcat are installed.
Permissions: Administrator access on the Domain Controller is required
📦Step 1: Dump the NTDS.dit and SYSTEM Hive
First, hop onto a Domain Controller and open an elevated Command Prompt. Make yourself a dump folder. I’m using C:\MGMT\ADdump for this example.
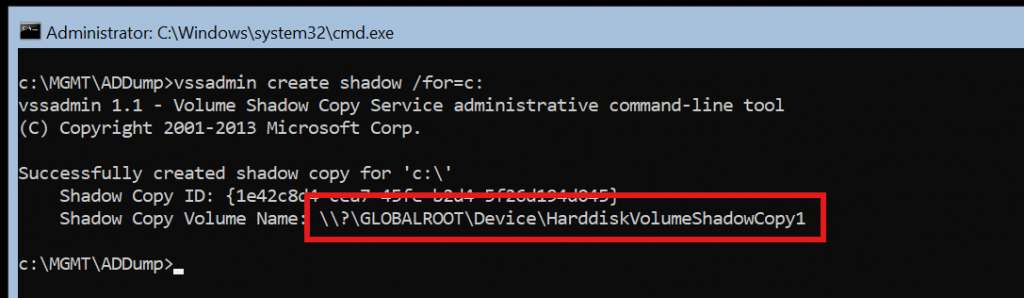
🗂️ Create a Shadow Copy
Windows wont let you directly interact with these system files so we have to create a snapshot of the C:\ then interact with that snapshot.
vssadmin create shadow /for=c:This will create a new shadow copy. Pay attention to the path it outlines as this will be different for each machine and time you do it depending on your setup.
📄 Copy NTDS.dit
copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\ntds\ntds.dit c:\MGMT\ADdump\ntds.dit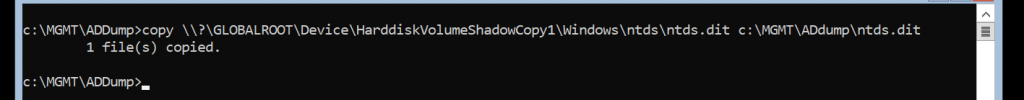
📄 Save the SYSTEM Hive
reg SAVE HKLM\SYSTEM c:\MGMT\ADdump\SYSTEM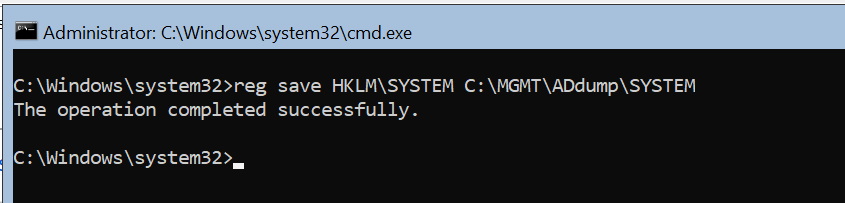
🧹 Delete the Shadow Copy
We now have the files we need but like a good sysadmin we need to clear up after ourselves. Remove the old snapshot from the system.
vssadmin delete shadows /allNote: If you regularly use Shadow Copies, delete just the one you made — don’t nuke them all.
Copy the ntds.dit and SYSTEM files over to your Kali box, then delete them from the DC. These are gold for attackers — don’t leave them hanging around.
🧪 Step 2: Extract Hashes with secretsdump
Were now going to use secretdump to extract all the data. All audit scripts and outputs will live in /opt/scripts/00-audit-ad/
Get your workspace in order. Here’s a folder layout I like:
/opt/scripts/00-audit-ad/
├── common # password lists and rules
├── ntds # your raw dump and output
└── output # cleaned and cracked resultsThe benefit of this is that only root can access these folders, when your finished you can just purge the ntds and output folders and still keep the password lists and rules.
Dump your ntds.dit and SYSTEM files into the ntds/ folder.
🛠️ Run secretsdump
impacket-secretsdump -ntds *location* -system *systemfile* -hashes lmhash:nthash LOCAL -output *filename*You will need to specify the path to the ntds.dit and SYSTEM file and give the extracted files a name.
impacket-secretsdump -ntds /opt/scripts/00-audit-ad/ntds/ntds.dit \
-system /opt/scripts/00-audit-ad/ntds/system \
-hashes lmhash:nthash LOCAL \
-output /opt/scripts/00-audit-ad/ntds/ext-ntlm
This will spit out a few files. The one we care about is ext-ntlm.ntds.
🧹 Clean the Dump
This file has a few extra columns in it so we need to clean up the file to only have usernames and the encrypted passwords.
cat *exportedNTDSfile* | cut -d : -f 1,4 > *outputfile*cat /opt/scripts/00-audit-ad/ntds/ext-ntlm.ntds | cut -d : -f 1,4 > /opt/scripts/00-audit-ad/ntds/clean-ntlm.ntdsBoom. Clean username/hash pairs, ready for cracking. You should now have a file called clean-ntlm.ntds
📚 Step 3: Get Your Wordlists & Rules
I use two password lists and 1 rule for my password cracking. Below are the links to each of them. Grab these and drop them into the common/ folder:
Optional: The Have I Been Pwned list. Just… good luck downloading it — it’s massive.
🧨 Step 4: Start Cracking
Now we want to try and crack the the database. Start with the basics and work your way up. We will try just the wordlists then start to include the rules.
hashcat -m 1000 --force *NTDS location* *PWNDDatabasefile* --username --potfile-path *potfile* --status🪨 Rockyou
hashcat -m 1000 --force /opt/scripts/00-audit-ad/ntds/clean-ntlm.ntds /opt/scripts/00-audit-ad/common/rockyou.txt --username --potfile-path /opt/scripts/00-audit-ad/common/cracked.pot --status💥crackstation
hashcat -m 1000 --force /opt/scripts/00-audit-ad/ntds/clean-ntlm.ntds /opt/scripts/00-audit-ad/common/crackstation.txt --username --potfile-path /opt/scripts/00-audit-ad/common/cracked.pot --status📚 OneRuleToRuleThemAll.rule
This is the cleaver part. The rule file takes each line of the password database and applies a set of rules to see if variations work. For Example.
Original: “password”
Transformed: “Password”, “P@ssword”, “P@55word”, “P@55w0rd001”
This is awesome but it requires some serious CPU power. Especially if you use the crackstation.txt file. I tend not to bother using the rule file on crackstation or haveibeenpwnd files.
As you can see below to possible passwords increases exponentially.
- RockYou alone: ~14 million
- With rule: ~745 billion
- Crackstation + rule: ~63 trillion (yep, with a T)
So yeah — check your CPU before diving in.
hashcat -m 1000 --force *NTDS location* *PWNDDatabasefile* -r *ruleFile* --username --potfile-path *potfile* --statushashcat -m 1000 --force /opt/scripts/00-audit-ad/ntds/clean-ntlm.ntds /opt/scripts/00-audit-ad/common/rockyou.txt -r /opt/scripts/00-audit-ad/common/OneRuleToRuleThemAll.rule --username --potfile-path /opt/scripts/00-audit-ad/common/cracked.pot --status🧾 Step 5: Show the Results
Once you have completed your various tasks you should then have a list of cracked passwords in your pot file. Use this to create a final output of cracked usernames and passwords.
hashcat -m 1000 --force *NTDS location* --username --show --potfile-path *potfile* --status -o *path to output file*hashcat -m 1000 --force /opt/scripts/00-audit-ad/ntds/clean-ntlm.ntds --username --show --potfile-path /opt/scripts/00-audit-ad/common/cracked.pot -o /opt/scripts/00-audit-ad/output/cracked-ad-accounts.txt
Now crack open that output file and see what you’ve got.
✅ Final Thoughts
Nice work — you’ve just done a proper Active Directory password audit. Hopefully everything looks clean, but if it doesn’t, now’s the time to go change some passwords and tighten the policy.
Don’t forget to delete everything sensitive when you’re done. These aren’t the kind of files you want lying around.
Regularly auditing passwords helps identify vulnerabilities before attackers do. Ensure you have robust password policies and educate users on creating strong passwords.
