So, we recently had our quarterly security scan. Somewhere down in the low-risk section of the report, I spotted an issue: weak SSH algorithms.
At first glance, I had two problems:
1. I wasn’t sure how to harden SSH to fix the weak algorithms.
2. I had no clue how to verify whether my fix actually worked.
I’ve used Kali for years—mostly in a “script kiddy” way, copying commands and processes from pentesters I’ve worked with. This time wasn’t much different
After studying the report and checking the screenshots of the vulnerabilities, I noticed the use of the ssh-audit tool. A bit of Googling later, and here’s what I came up with.
Prerequisites
If you haven’t already, make sure you have a VM running Kali. This is such a great tool for auditing your security and scanning the network for vulnerabilities.
Installing ssh-audit
Step 1: Update Kali and its package list:
sudo apt-get updateStep 2: Install ssh-audit:
sudo apt-get -y install ssh-auditUsing ssh-audit
With ssh-audit installed, I can start replicating the test results from the pentest.
To run a basic scan, just use:
ssh-audit <IP address>This runs a default sweep of the target and gives you a Red / Amber / Green style report.
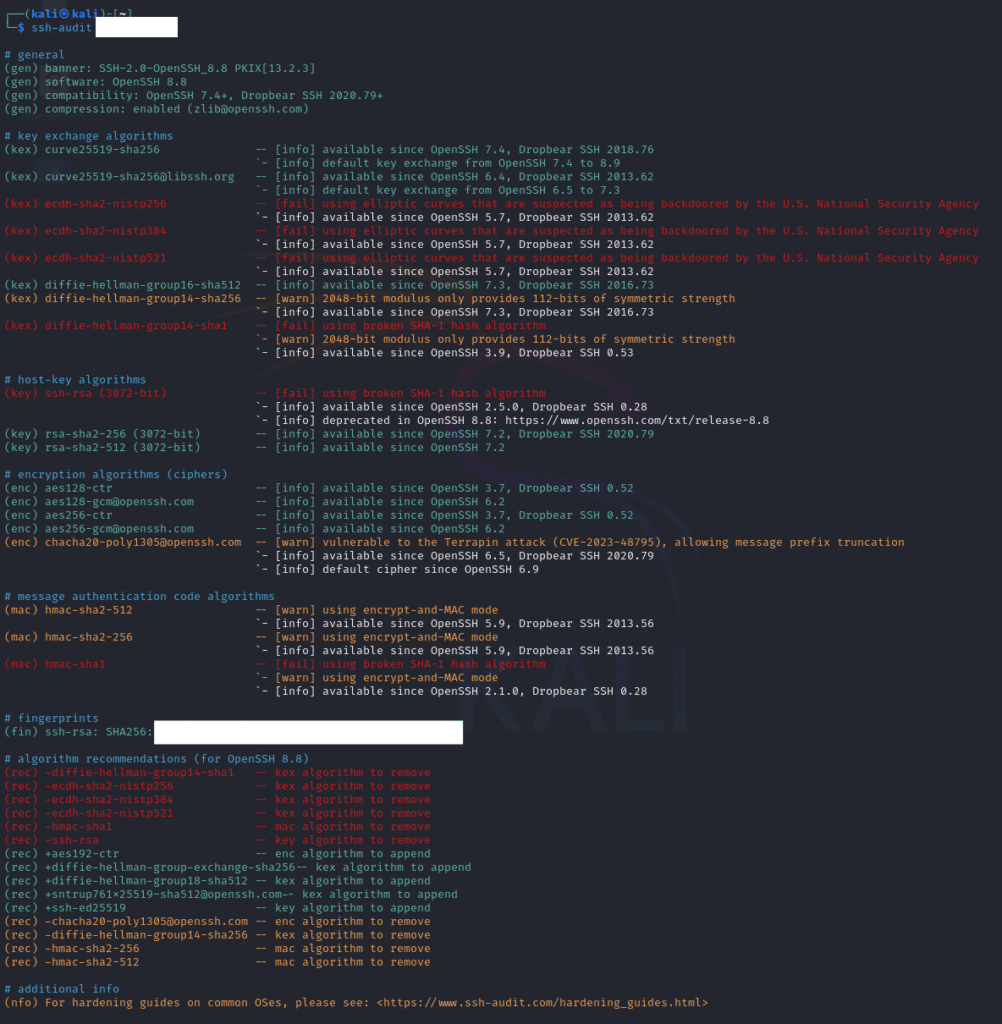
As you can see—yeah, not great. But the good news is, the tool lists recommendations at the bottom. Apply the remediations, retest, and keep going until things look better.
How I fixed everything is a whole other post, but after a lot of back and forth… here’s the end result.
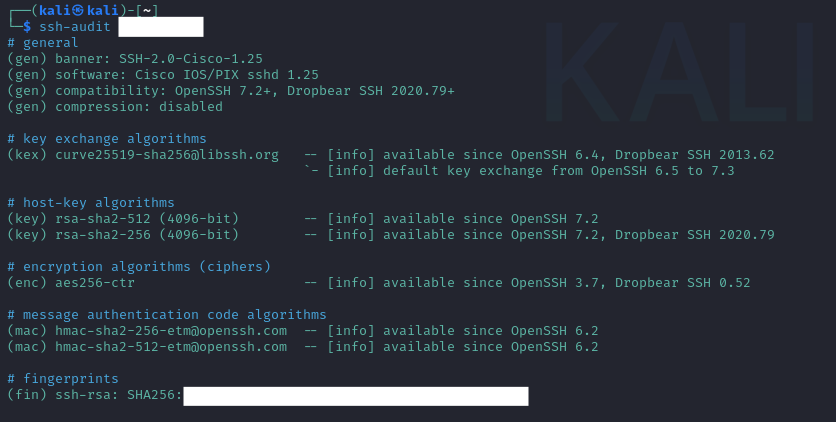
“Mastering” ssh-audit
There isn’t really much to master here, but a useful feature is auditing a list of IP addresses.
I ran Masscan to create a list of IPs on the network responding to SSH port 22. These were all in a file called “ssh-ips.txt”
